
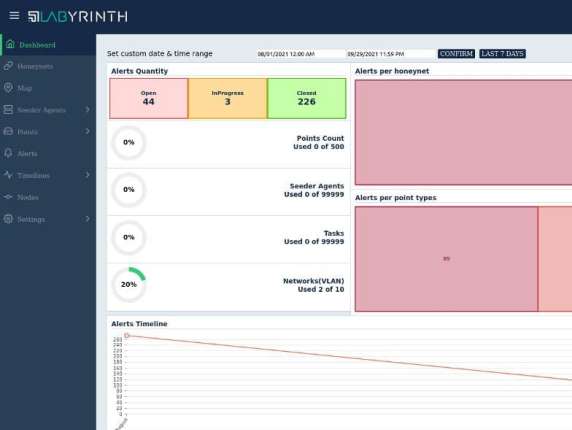
Labyrinth detect and respond to hacking activities, defending core assets from compromise.
Using deception technology, our Platform provides security teams with a simple and efficient tool for the earliest possible detection of attackers inside corporate networks.
-
Threat Detection : Unauthorized Access, Vulnerabilities Exploitation, Command-and-Control attacks
-
Data Gathering and Analysis: Threat identification, Pattern analysis, Content analysis
-
Automated Response: Generation of threat indicators, Isolation of compromised hosts, Incident Logging and Reporting
Why Labyrinth
Labyrinth provides adversaries with an illusion of IT services and applications vulnerabilities to provoke them for actions, detects and monitors all their activities, and isolates them from real IT network.
-
NO long implementation process
Simple installation and configuration – ready to work in hours, not days
-
NO terabytes of data to store
The Platform gathers only valuable data related to security incidents
-
NO overwhelming security alerts
The solution is silent until it is being touched, so does not generate “digital noise”
-
NO false-positive warnings
Labyrinth provides security teams with highly reliable alerts with less than 1% false positives
-
NO special skills needed
Intuitive interface provides full real-time attack visibility
Labyrinth’s unique features ensure the protection of your applications and services on-premise and in the cloud.
Extended detection capabilities
The Platform provides attackers with a broad range of fake application and service vulnerabilities to increase the attack surface and ensure all the possible attack vectors covering.

Advanced WEB application protection
Labyrinth embedded a unique technology which allows providing additional leer of security for the most desired by hackers target – WEB based applications and services.
Active Defense
Client Honeypots are active security devices using for search of malicious servers attacking clients and MITM detection. They pose as a client and check whether an attack has occurred.
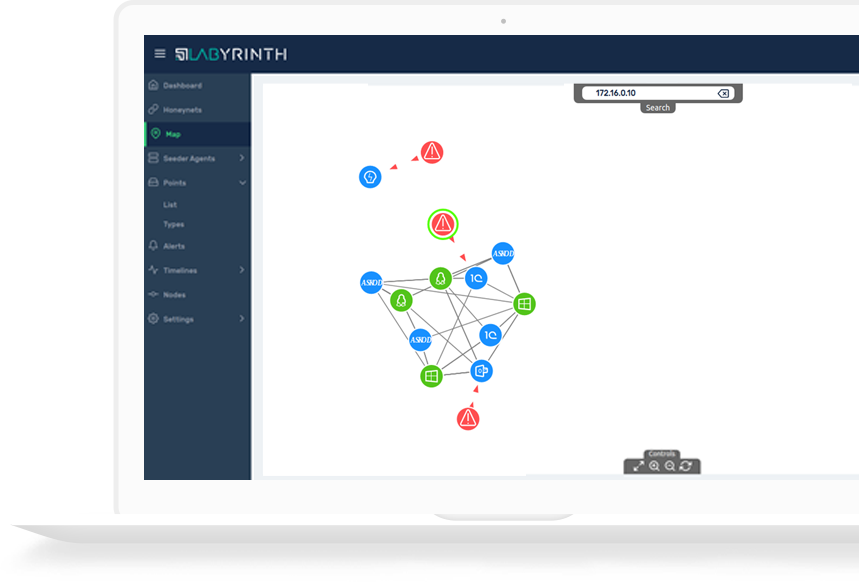
Labyrinth Deception Platform
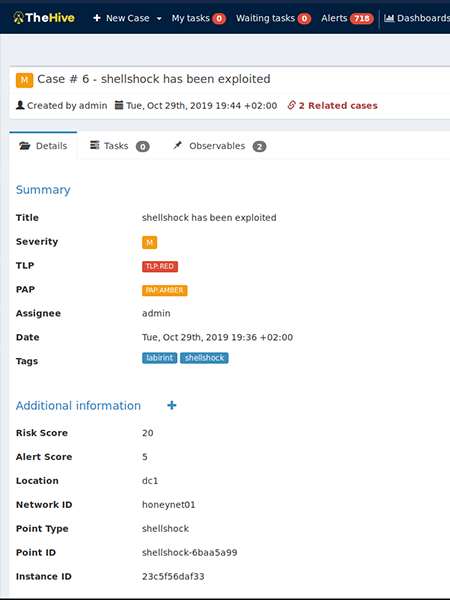
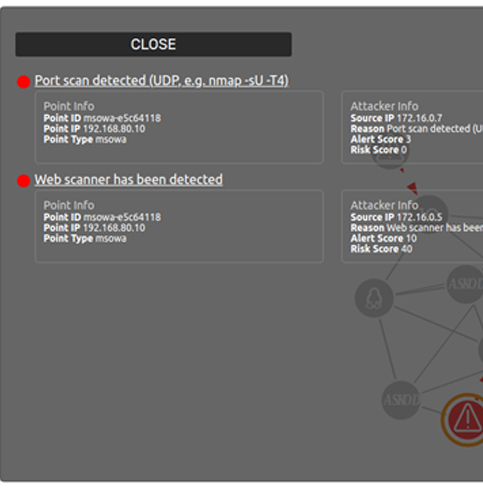
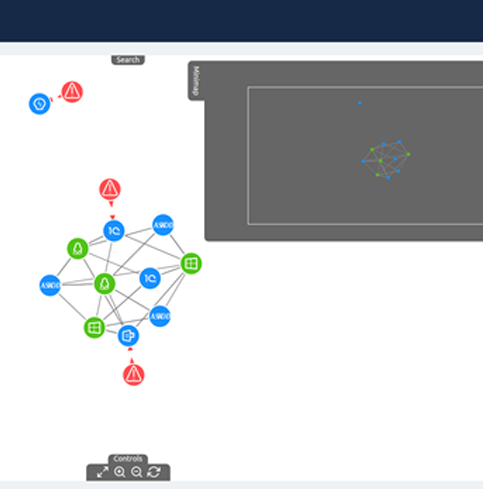
Labyrinth Deception Platform changes an attack surface providing adversaries with an illusion of real infrastructure vulnerabilities. Each part of the imitated environment reproduces the services and content of a real network segment. The solution is based on Points – smart imitation hosts that mimic special software services, content, routers, devices, etc. Points detect all malicious activities inside a corporate network providing comprehensive coverage of all the possible attack vectors.
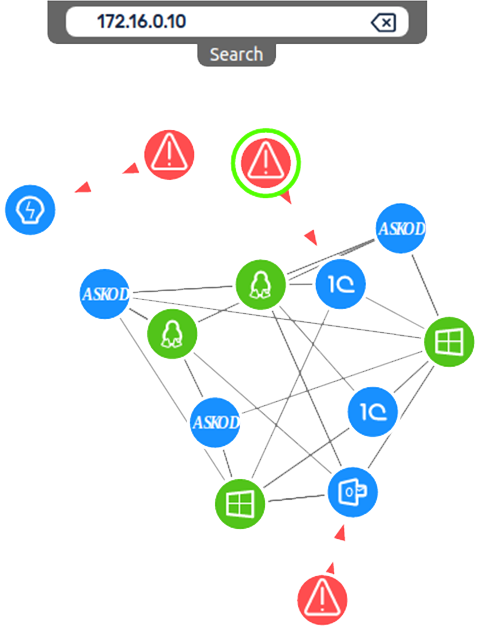
Labyrinth provokes the attacker for actions and detects suspicious activities. While an attacker proceeds through the fake aim infrastructure, the Platform captures all the hostile’s details. The security team receives information about threat sources, the tools that were used, and about exploited vulnerabilities and the attacker’s behavior.
Detection
-
Reconnaissance activities
-
Unauthorized Access Attempts
-
Vulnerabilities exploitation
-
Command and Control Attacks
Data Gathering and Analysis
-
Pattern analysis
-
Access tries
-
Behavior analysis
-
Content analysis
Labyrinth deception platform advantages
-
No need for infrastructure: Does not require the collection of a huge amount of data; Gathers only data related to security incidents; Zero impact on IT network recourses productivity;
-
No overwhelming alerts: Does not generate “digital noise”; Extremely low false positive rate; Provides full real-time attack visibility.
-
No deep expertise needed: Simple installation and configuration; No special skills needed to use the solution; Automated detection and response.
Response
-
Full investigation support
-
Automatic generation of threat indicators
-
Isolation of compromised hosts
-
Report Generation
Solutions
SMB
Labyrinth can be used as a single solution for implementing detection and response security measures on network leer, providing provides real-time security incident visibility without generating overwhelming alerts. Through third-party integrations with NGFWs and EDRs, Labyrinth allows isolated threats from the IT network. To accelerate incident response and forensic, the necessary data can be automatically sent to IRMS.
SOC
Labyrinth Deception Platform enriches collected data about incidents and sends to SIEM aggregated event information, providing security teams with the ability to prioritize alert processing. Integration with SIEM also gives an opportunity to receive additional information about detected suspicious activities for getting greater visibility on the chain of events within a security incident.
MSSP
Labyrinth Worker can be located on a client’s side, while Admin Server, IRMS, SIEM – hosted by MSSP provider, allowing the provider:
-
fully manage configuration and observe the current status of subsystems;
-
respond to incidents immediately after detection, without the involvement client’s engineers
integrate the platform with third-party systems to improve the response quality using the functionality of the other information security products (NGFW, EDR, WAF, etc.)
Resources
Comprehensive insights on deception technology, active defence, and how to beat adversaries at their own game.

